We have created a collection of informative and detailed video tutorials to help you explore InControl. These videos cover a wide range of topics and are designed to make it easier for you to learn and use the platform.
Whether you are a beginner or an experienced user, our videos will provide valuable insights into InControl's functionalities and features. From registering your first node to understanding security compliance and vulnerability assessment, our step-by-step instructions will guide you through each process.
With InControl, you can ensure that your system meets security standards and identify potential vulnerabilities. Our videos provide a comprehensive overview of the platform, empowering you to take proactive measures to protect your system.
Start enhancing your system security by watching our videos now. Let us be your trusted companion in navigating InControl.

In this concise yet informative video tutorial, we will guide you through the process of registering your first node in InControl. By following the step-by-step instructions provided, you will not only successfully register your node, but also gain valuable insights into the security compliance and vulnerability state of your system.

Bert Hajee
Oct 8, 2023 · 7 minutes duration
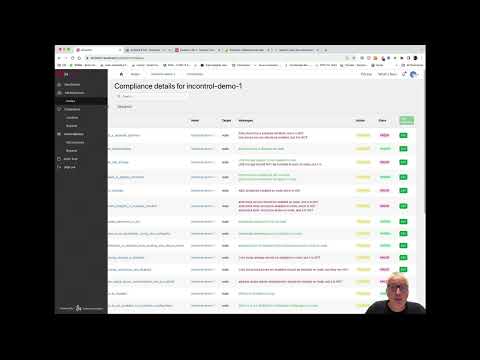
After InControl has completed a compliance scan on your system, it will present you with the current compliance status of your system. This includes a wealth of information regarding the security of your system. In this brief video, we will elaborate on the types of information available and how it can assist you in enhancing the security of your system.

Bert Hajee
Oct 9, 2023 · 4 minutes duration
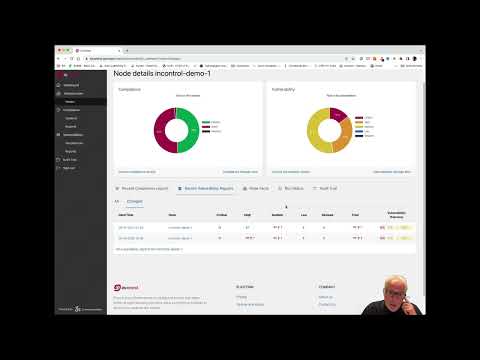
After InControl has conducted a vulnerability scan on your system, it will provide you with an overview of the current vulnerability status. This will include information on the number of critical and high vulnerabilities detected, as well as the files on your system that are affected. This step is crucial in addressing and resolving these vulnerabilities.

Bert Hajee
Oct 9, 2023 · 3 minutes duration



